AES-128 Encryption and Decryption Using Verilog
Abstract
Abstract
AES-128 Encryption and Decryption Using Verilog

Mentors: Anshul K, Karthikeshwar Nadh Mellacheruvu , Geedhara Ram Rithesh Reddy
Mentees: Vibhu Kav Bhat, Abhishek Agrawal, Pratheek Acharya, Kushagra Agrawal, Priyanshu Minz, Ashritha OR
Introduction
The Advanced Encryption Standard (AES) is one of the most widely used cryptographic algorithms for securing digital communication. It consists of multiple transformation rounds applied to 128-bit data blocks. This project implements the AES-128 algorithm in Verilog, focusing on a modular and maintainable structure that supports both encryption and decryption paths.
Literature Survey and Technologies Used
- AES Standard: Defined by NIST in FIPS-197.
- Technologies Used:
- HDL Used: Verilog
- Design Tool: Xilinx Vivado
- Simulation Tool: Vivado Simulator (XSIM)
- Reference Designs: Reviewed existing open-source AES implementations and academic papers on cryptographic hardware design.
- AES Algorithm Overview: Consists of 10 rounds for AES-128, with key transformations including SubBytes, ShiftRows, MixColumns, AddRoundKey, and corresponding inverse operations.
Methodology
The implementation divides the AES algorithm into several standalone modules:
- sub_bytes.v
- shift_rows.v
- mix_columns.v
- key_expansions.v
- InvSubs.v
- InvShiftrows.v
- InvMixColumns.v
These modules interact in a top-level controller "AES_128_top.v" that performs the encryption or decryption in sequential steps.
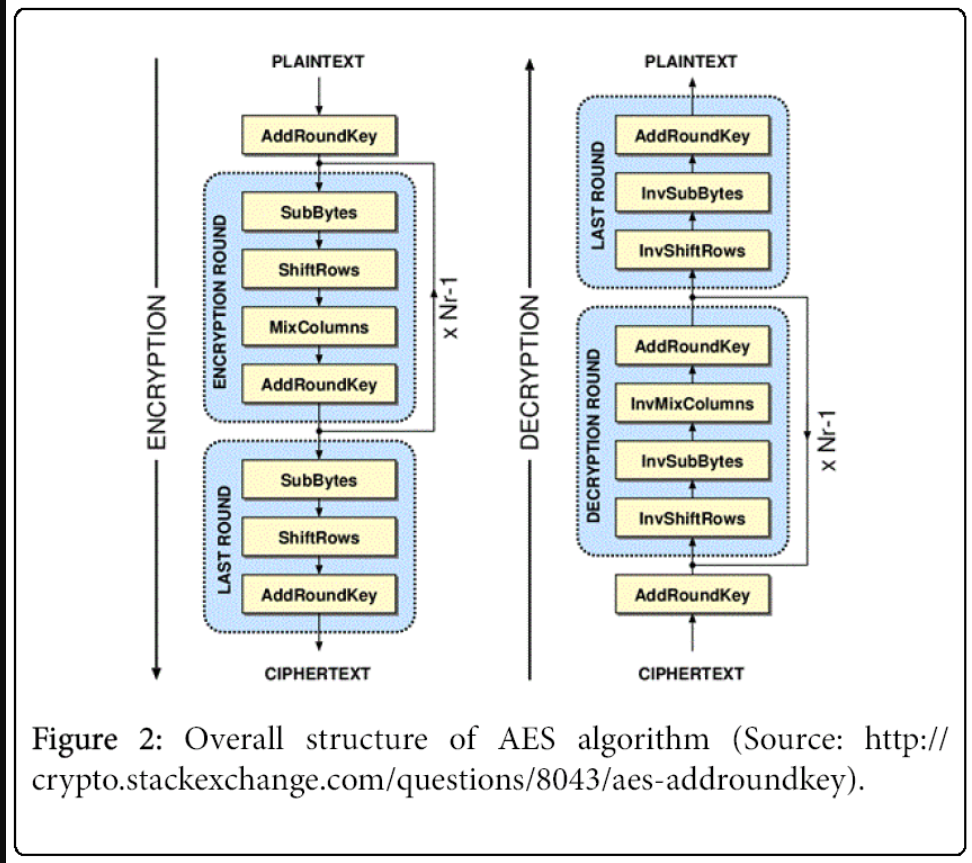
- SubBytes and InvSubBytes
- Implemented using sub_bytes.v and InvSubs.v.
- Utilizes lookup tables defined in gpt_sbox.v for performing byte substitution using the AES S-box and its inverse.
- ShiftRows and InvShiftRows
- shift_rows.v cyclically shifts rows of the state matrix to the left.
- InvShiftrows.v reverses this operation during decryption.
- MixColumns and InvMixColumns
- Implemented in mix_columns.v and InvMixColumns.v.
- Performs finite field matrix multiplication over GF(2^8) to diffuse the bytes.
- The inverse performs the reverse matrix multiplication.
- . AddRoundKey
- A simple XOR operation between the state and round key, implemented within the top module.
- Key Expansion
- Implemented in key_expansions.v.
- Dynamically generates the necessary round keys from the original 128-bit key using Rcon and S-box transformations.
- AES Top Module
- AES-128 top.v serves as the main controller, managing the round flow (10 rounds for AES-128) and integrating all transformation modules.
- Supports both encryption and decryption based on a control signal.
- Control Logic
- The top module includes internal state management and a counter to control the round number.
- Encryption starts with AddRoundKey and ends after the 10th round.
- Decryption follows the reverse order, using inverse transformations appropriately.
Simulation and Verification
The design was verified using testbench.v.
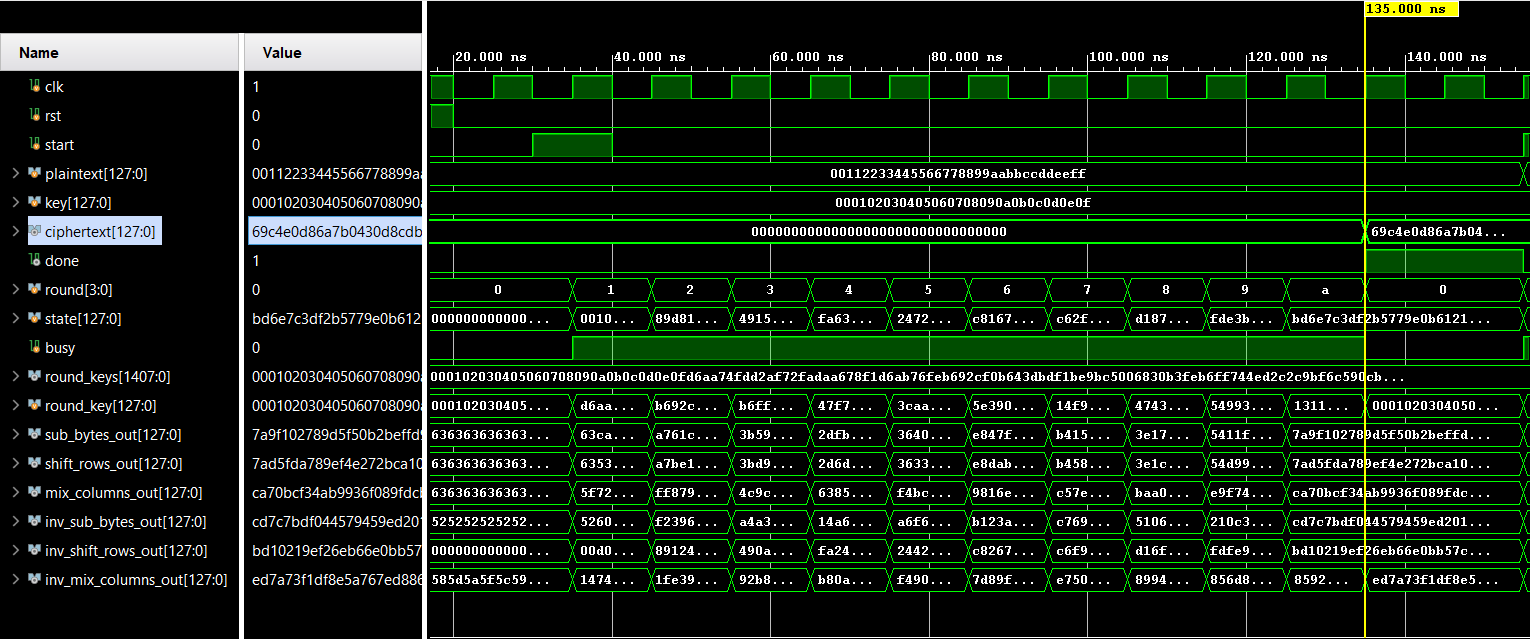
Standard AES test vectors were applied:
Plaintext: 00112233445566778899aabbccddeeff
Key: 000102030405060708090a0b0c0d0e0f
Expected Ciphertext: 69c4e0d86a7b0430d8cdb78070b4c55a
The output of encryption was fed back as input to the decryption module to validate full-cycle correctness.

Ciphertext:69c4e0d86a7b0430d8cdb78070b4c55a
Key: 000102030405060708090a0b0c0d0e0f
Expected Plaintext:00112233445566778899aabbccddeeff
NOTE:ciphertext is just the name for the output and plaintext is the name for the input in the waveform and is technically the plaintext in case of decryption
Key Aspects
Modularity: Each transformation in AES is implemented in a separate Verilog module to promote reusability and clarity.
Testbench: A testbench provides test vectors to verify the correctness of the encryption process.
Key Expansion: Implemented statically for AES-128, where the round keys are generated at runtime.
.
Results
- Functional Accuracy: The AES modules were validated against known plaintext-ciphertext pairs and passed all test cases using testbench.v.
- Simulation Output: Waveforms verified correct sequential application of AES rounds and transformations.
Conclusions
- The project successfully implements AES-128 encryption and decryption using Verilog.
- The modular architecture ensures code clarity and ease of debugging.
Future Scope
- Pipelining: Introduce pipeline stages between transformation modules to improve throughput.
- Extended Key Sizes: Add support for AES-192 and AES-256.
- FPGA Deployment: Map the design onto FPGA hardware for real-time data encryption.
- Power Optimization: Evaluate trade-offs in resource usage and power consumption.
Resources Used
- DSD
- Verilog
- https://zerofruit-web3.medium.com/what-is-aes-step-by-step-fcb2ba41bb20
- https://engineering.purdue.edu/kak/compsec/NewLectures/Lecture8.pdf
GitHub Repository
All the simulation files and source codes can be found here.
Report Information
Report Details
Created: May 23, 2025, 12:15 a.m.
Approved by: Aniruddh Muralidhara Kamath [Diode]
Approval date: May 25, 2025, 12:23 p.m.
Report Details
Created: May 23, 2025, 12:15 a.m.
Approved by: Aniruddh Muralidhara Kamath [Diode]
Approval date: May 25, 2025, 12:23 p.m.

